TP-Link Deco M5 Hardware Hacking
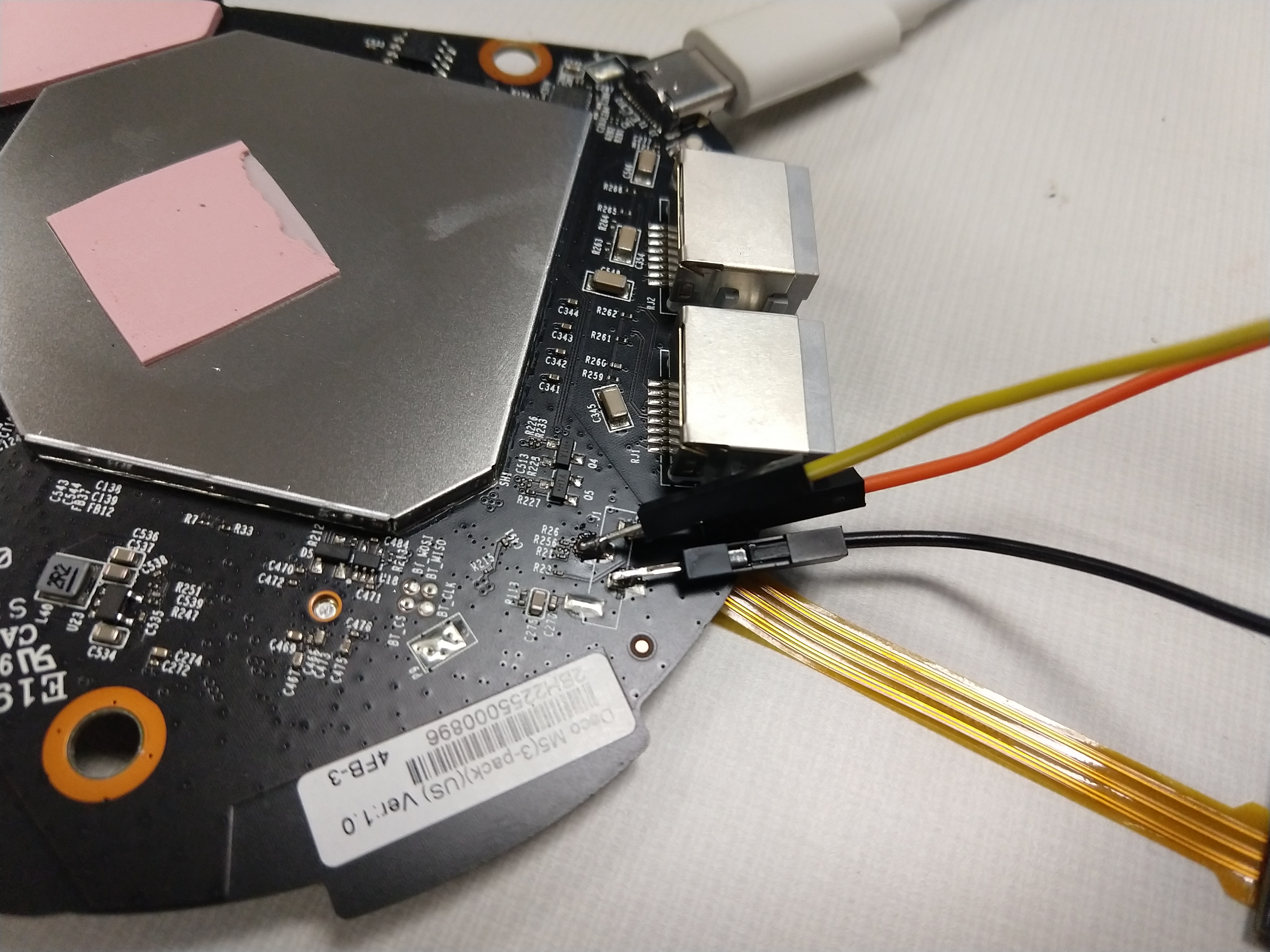
As part of a graduate reverse engineering course at university, my group was tasked with auditing the security of TP-Link's mesh wireless offering, the Deco M5. One of the chosen avenues was to attempt gaining root shell access by interfacing with an exposed debug interface on the device. This post …