TP-Link Deco M5 Hardware Hacking
As part of a graduate reverse engineering course at university, my group was tasked with auditing the security of TP-Link's mesh wireless offering, the Deco M5. One of the chosen avenues was to attempt gaining root shell access by interfacing with an exposed debug interface on the device. This post will highlight the findings of this process.
First, the top cover comes off. After a bit of wrangling with the plastic cover using a guitar pick, all of the plastic latches were disengaged, and the cover came off. This was done gently as to not rip the ribbon cable which controls the top dome's LED.
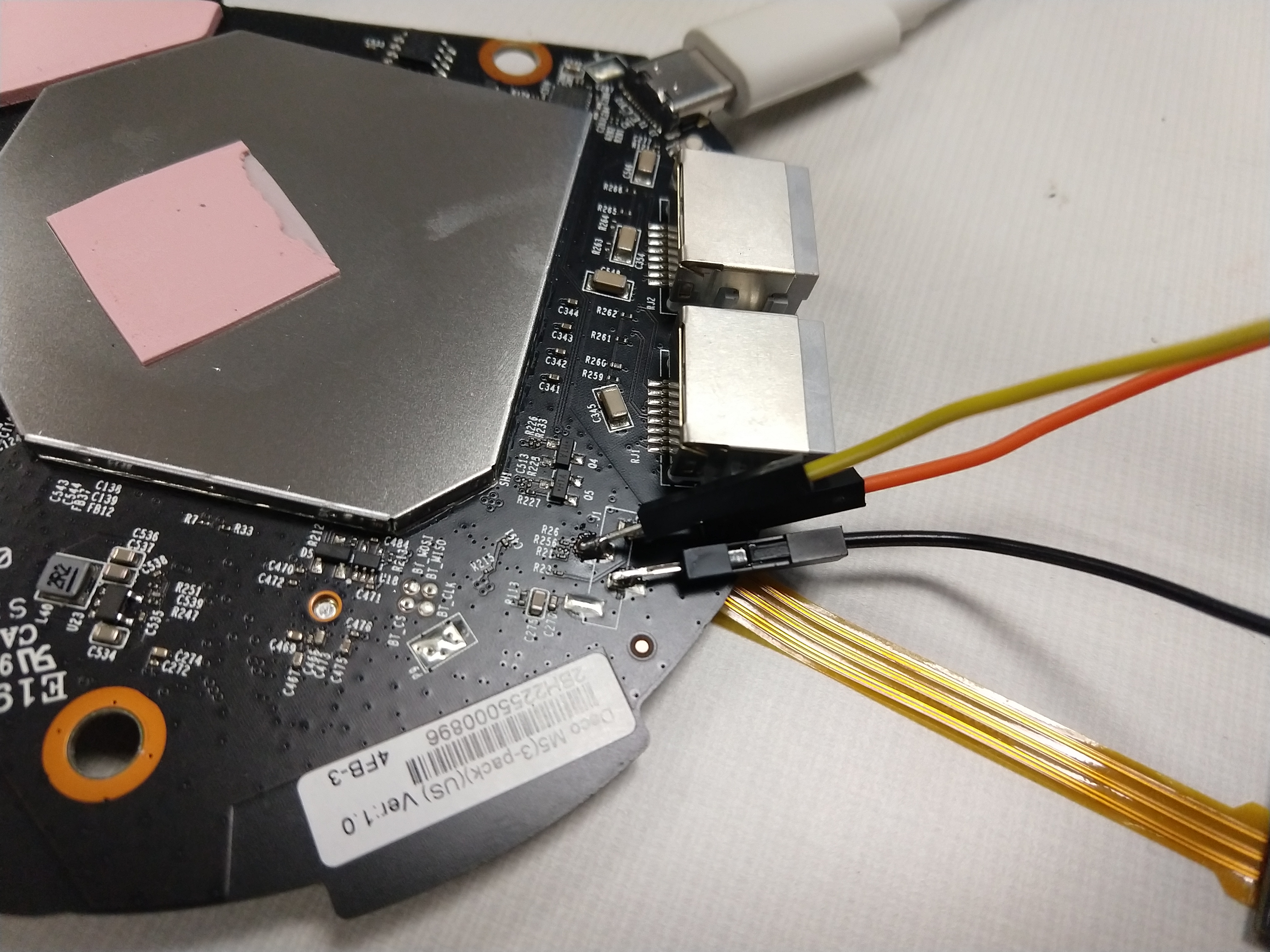
Immediately after removing the cover, a 5-pin header is exposed, labeled J2, as pictured below towards the upper left. After probing the header with a multimeter and other tools, it appears to be powered, but was not recognizable as a known interface.
Embarrassingly, while probing these pins with a multimeter, we managed to fry two devices by accidentally and momentarily shorting a GND pin with a 3.3V pin. The pins are very close together, thus requiring patience and a steady hand. The voltage regulator appeared to be fried, since it was no longer converting 5V into 3.3V, but other components appeared to be damaged as well since a supplemental power supply did not provide expected results.
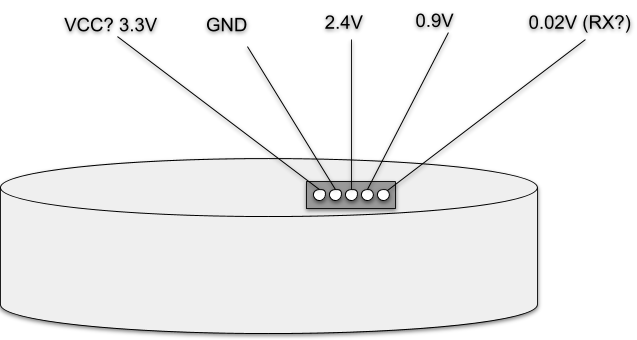
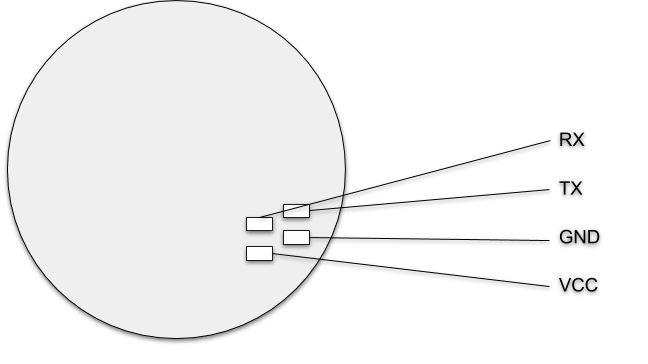
See the rough diagram of measurements below.
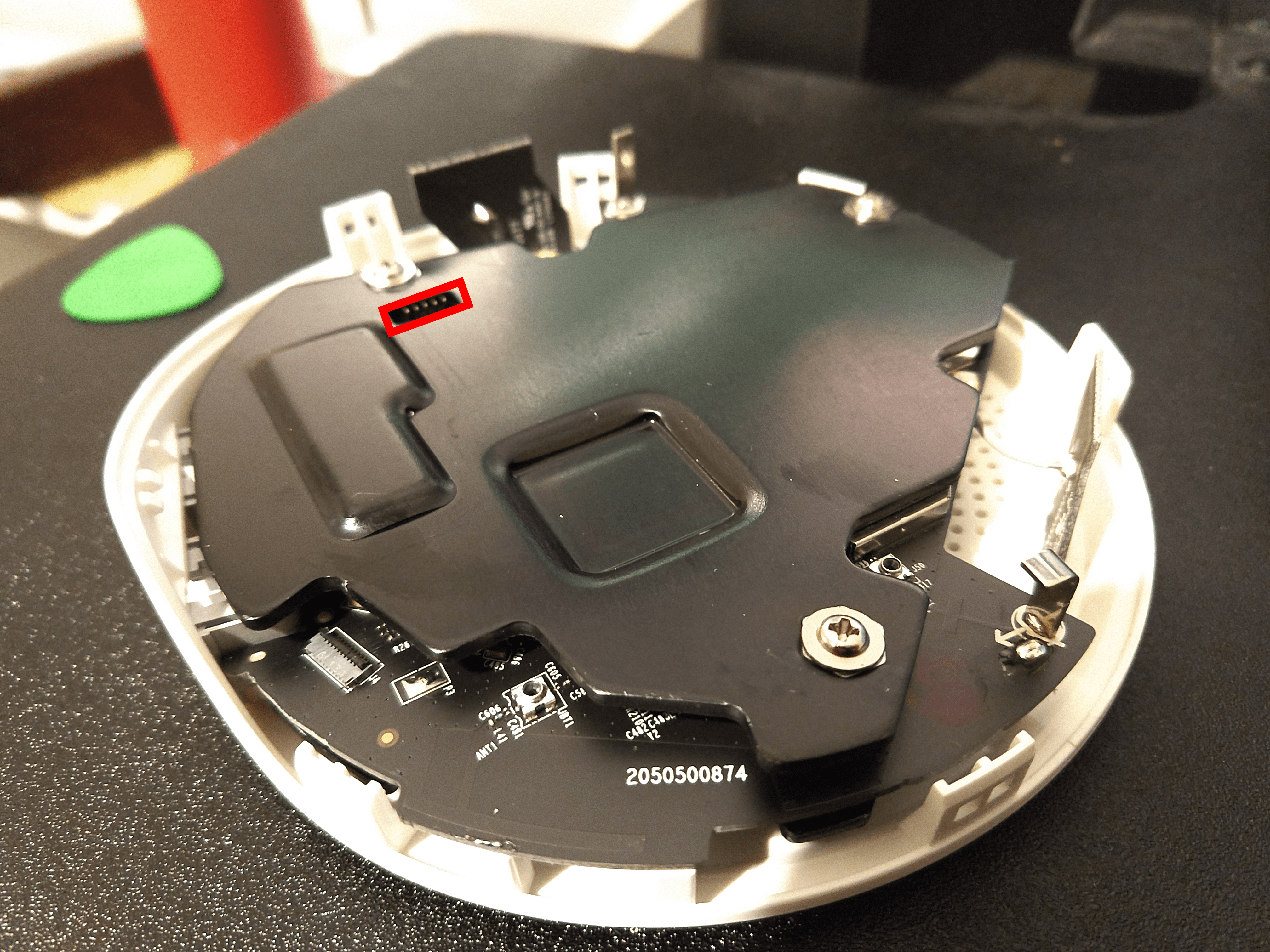
After removing the top heatsink and the PCB itself, a second interface with four pads is exposed on the bottom.
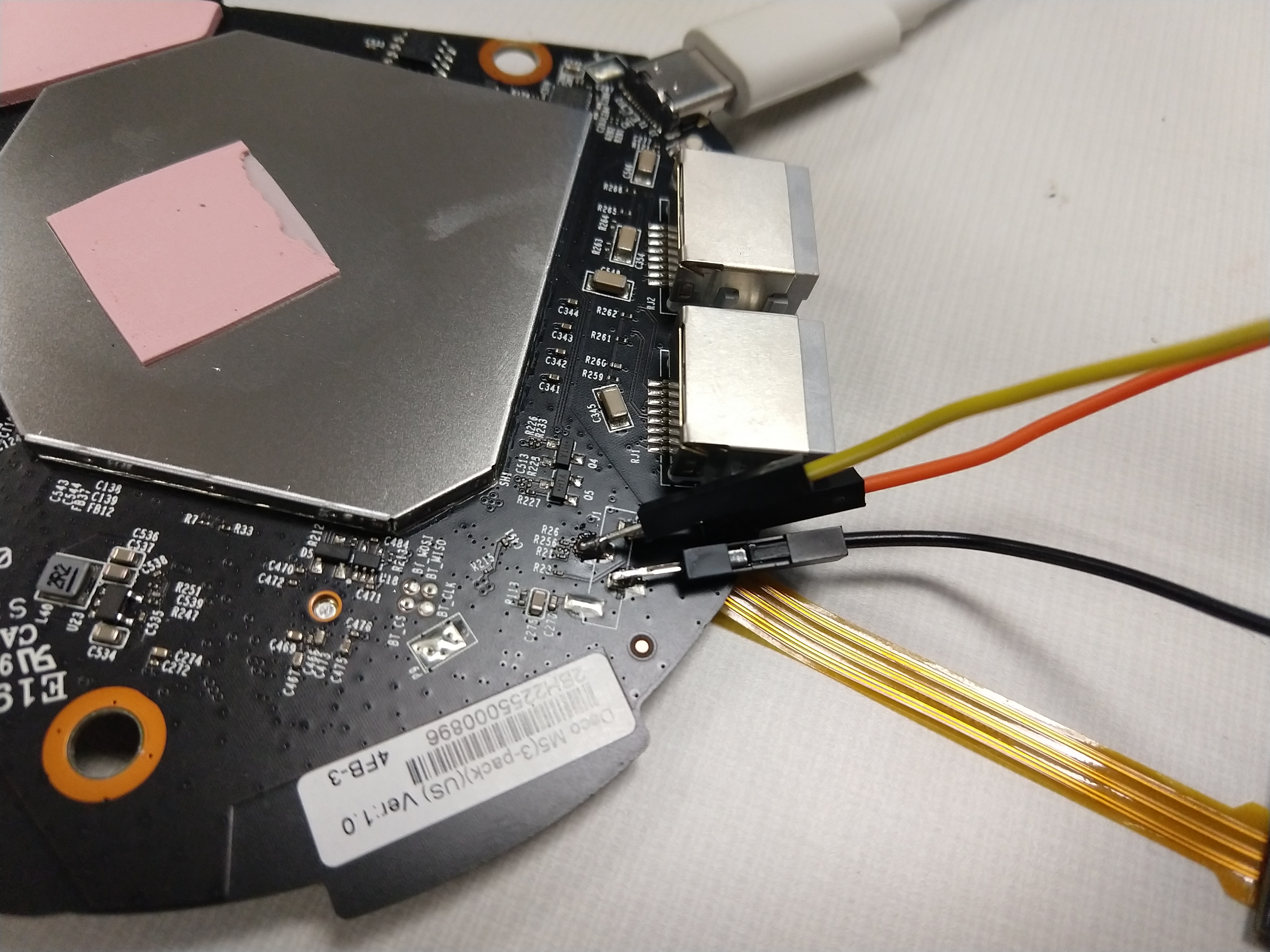
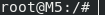
The measurements were textbook serial, as seen below.
After attaching an FTDI FT232RL and using the standard baud rate of 115200, root access on the device was obtained!